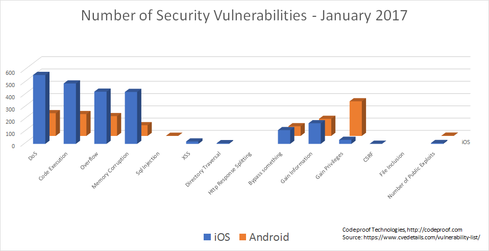
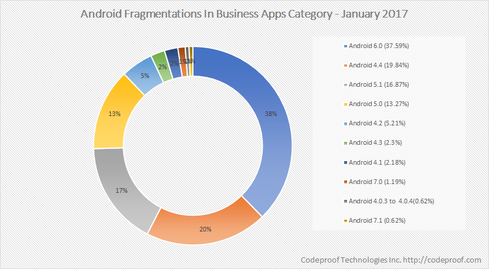
Sure, apps are convenient. But when not properly assessed, they can cause security holes.
As the app frenzy that captivated consumers now blazes through the business world, it’s creating an unfortunate by-product: disconcerting security blunders and disasters.
After realizing apps boost businesses by simplifying life for employees, partners, and customers, organizations are feverishly “appifying” their operations: order management, payments, inventory control — you name it. But in their rush, many companies aren’t rigorously assessing the security of these Web and mobile apps, despite their multiple links to critical back-end systems and data.
The Road to Hell Is Paved with Insecure Apps
With the app era’s benefits also comes a tremendous potential for danger, if vulnerabilities exist in those interconnection points. Bad actors are looking to exploit these security gaps and sneak in through the app door.

Compared with other attack patterns, Web app attacks have become the most likely to trigger a data breach, according to Verizon’s 2016 Data Breach Investigation Report. This means Web apps aren’t just exposed, but “disproportionately vulnerable” compared to other attack vectors, according to Verizon. Furthermore, Ponemon Institutefound that data breach costs to organizations jumped almost 30% since 2013 to $4 million on average per incident in 2016.
Let’s shift now from the big picture and zoom in on two app security failures of which I have firsthand knowledge.
A Bank Winds Up with Egg on Its Face
When I was at a previous job, a large bank called me in to help after a faulty app turned a seemingly simple project into a nightmare. Seeking more shareholder participation in proxy voting, the bank decided to make the process more convenient with a mobile app. The bank accepted a low bid from a fledgling contractor and didn’t specify security requirements, except to give the app a sign-in gate. Incorrectly assuming the app had been built with native authentication, the bank distributed it to investors, without reviewing its code or development process.
What the bank didn’t know was that the contractor had used a flawed authentication library available online, which stealthily transferred contacts on users’ phones to a third-party server in China. The bank found out only after scammers flooded its shareholders with phishing attacks.
What’s Inside My Sushi Roll? Phish?
App fiascos aren’t limited to large organizations. When small companies ignore security, consequences can be disproportionately large.
I recently received an email resembling a FedEx notification, but the tracking number format looked strange. Upon further inspection, I found that the “track package” and “unsubscribe” links pointed to a Singapore sushi roll shop’s WordPress website with an open “file upload” function. A hacker, likely armed with a simple script, found the Web app’s vulnerability — the site builder’s mistake — uploaded malicious code, and crafted the phishing attack. I didn’t fall for this one, but others likely did. Study after study reveals disturbingly high success rates for phishing scams.
The RSA Q2 2016 Threat Report, released in September, found the following:
- 1 million+ unique phishing attacks were identified in the prior 12 months — one every 30 seconds.
- In the second quarter of 2016, phishing attacks jumped 308% year-on-year.
- The total cost to global organizations from phishing was $9.1 billion.
See, Assess, and Remediate
Before the cloud and mobility revolutions, applications had simpler, linear architectures, which made securing them easier. Today, apps are intertwined with other apps, Web services, and legacy back-end systems via APIs and custom integrations. They also expose many more functions to many more people via the Internet. This makes them a conveniently accessible target for hackers. The result: it’s much more complicated to find security gaps and weak links.
Consider these three areas where you can take concrete steps to build a safer enterprise and a culture of clean code.
Focus Area #1: See
You need full, uninterrupted visibility into all your applications, whether they were purchased or developed internally. A comprehensive, continuously updated app inventory puts you in control to manage apps’ security. This means understanding development methods and frameworks employed, and knowing all the modular components within the apps. That way, when vulnerabilities affecting these components are disclosed, you’ll know instantly which among your apps are affected.
Visibility also means understanding the threats posed by the Web of third-party service and resource interconnections tapped by your apps. For example, the bank would have avoided embarrassment if it had bothered finding out the components the contractor had used in the app and understood their risks.
Focus Area #2: Assess
Assessment involves probing your apps with a broad, deep scope and getting many parties involved, including app dev, quality assurance (QA), and information security. To reduce coding errors and catch most other ones before code makes it to production, you should do the following:
- Train QA staffers in Web application assessment
- Teach developers secure coding techniques
- Invest in continuous integration environments to automate and accelerate code development and testing
Assessment is an area where the Singapore shop failed badly, as it couldn’t detect a glaring flaw in its website that hackers exploited for a phishing campaign.
Focus Area #3: Remediate
Organizations need to prioritize remediation granularly. They can’t just focus on “crown jewel” apps. Simple code reused in many apps poses threats if it contains vulnerabilities. Remediation also presents an opportunity to promote using secure components and make everyone on the team feel empowered to protect the organization. Finally, the remediation process highlights successes and failures, so you can take steps to continually improve.
The bank and shop can learn valuable lessons from their app blunders and remediation, and lead them to adopt new app security best practices, processes, and tools.
Promise, Not Peril
In the end, don’t lose sight that the goal is to create a safe, efficient environment where the promise of the app era is realized and the peril is diminished.
Related Content:
Jason Kent is Vice President, Web Application Security Product Management at Qualys. Prior to that, he held technical security positions at Veracode, BlueCoat, Aruba, and Verizon. Through more than a decade of dedicated AppSec experience, he has established expertise in … View Full Bio
Article source: http://www.darkreading.com/application-security/the-promise-and-peril-of-the-app-era/a/d-id/1328061?_mc=RSS_DR_EDT