K-12 Study Gives Schools Low Marks for Protecting Student Privacy Online
A new study released today by EdTech Strategies found that the websites of leading state education departments and local school districts lack even the most basic online security and privacy protections.
Douglas Levin, president of the Arlington, Va., consulting group, says his study comes out in the context of an intense discussion the past several years about the online privacy of students.
“We need to protect students, but in many ways that is too narrow a focus,” Levin says. “Keep in mind that technology is used at school districts for human resources, food, health and transportation, and it is also used by educators and parents.”
Levin based the study on automated and manual reviews of the 50 state department of education websites and the websites of 159 K-12 school districts nationally. The study, “Tracking EDU: Education Agency Website Security” was conducted from October 2017 to January of this year.
Here are some highlights from the study:
Lack of secure browsing. Most state and local education websites do not support secure browsing, which puts both schools and websites at risk. And, at least 12 states offer no HTTPS support for secure browsing: Arkansas, Connecticut, Kansas, Maryland, Mississippi, Nevada, New Mexico, Oklahoma, Rhode Island, Vermont, Virginia or Washington.
Widespread use of tracking cookies. Virtually every state and local district (158 out of 159 tracked) has partnered with online advertising companies to deploy sophisticated user tracking and surveillance on their websites. Many states and the vast majority of local school district websites do not disclose the presence and nature of this ad tracking and user surveillance, or the mechanism for how users can opt out of these data collections.
Absence of privacy policies. Nearly 15% of state department of education websites do not publish a privacy policy of any kind. Of the 43 state agencies that publish a privacy policy, only 32 disclosed the use of ad tracking or surveillance cookies.
Noncompliance with Google terms of service. Despite the near universal deployment of Google Analytics on state and local education websites, only four state and two local school districts were found in compliance with Google’s terms of service which require specific privacy-related disclosures by its customers to their users, including what data is collected, and how users can opt out.
Moving forward, Levin says K-12 state departments of education and schools district should consider deploying HTTPS to offer more secure web browsing, and find ways to notify users of the presence of ad trackers. He says the websites posted by the states of Maine and Utah demonstrate that state and local agency websites can offer meaningful experiences to parents, educators and other stakeholders that offer privacy without resorting to invasive and undisclosed ad tracking. Maine, for example does not record personal information without the user’s permission.
Follow this link for a more complete list of action items.
Related Content:
- 6 Tips for Building a Data Privacy Culture
- Privacy: The Dark Side of the Internet of Things
- Why Your Business Must Care about Privacy
Steve Zurier has more than 30 years of journalism and publishing experience, most of the last 24 of which were spent covering networking and security technology. Steve is based in Columbia, Md. View Full Bio
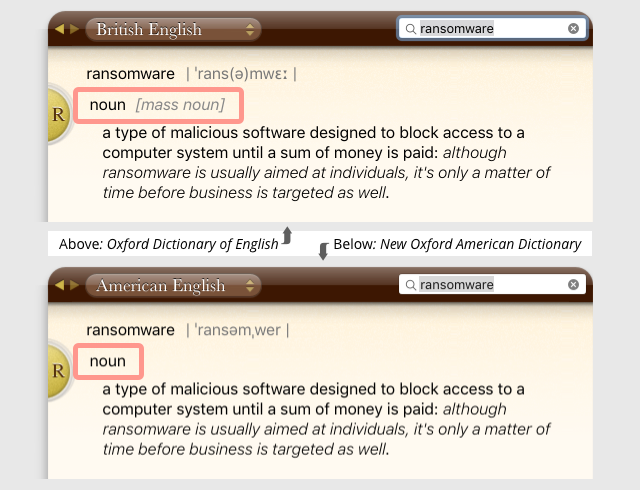
 What else made it into the OED for 2018?
What else made it into the OED for 2018?
 What else made it into the OED for 2018?
What else made it into the OED for 2018?