To hack Australia and learn its secrets, buy second-hand furniture
The Australian government has suffered what must as one of the most ridiculously embarrassing security breach in its history: cabinet records from five successive governments were sent to a second-hand furniture store.
The trove ended up in the hands of the Australian Broadcasting Corporation (ABC – which is in the process of publishing what it judges safe to publish here).
It appears that someone decided to sell two filing cabinets intact because they’d lost the key (really); the buyer applied a power drill to the locks, and the rest is history.
And what a history it’s turned out to be: for the ABC. The broadcaster says it’s “withheld documents if there are national security reasons, if the information is already public, or to protect the privacy of public servants.”
The Department of Prime Minister and Cabinet has already issued a statement saying it will investigate the incredible idiocy that made this possible what happened and won’t comment further for now.
Early NBN negotiating notes among the goodies
Among the documents revealed by the ABC are details of confidential briefings about how the Rudd government intended to fund Australia’s always-controversial National Broadband Network (NBN).
This needs context: in 2009, when it first conceived a universal fibre-to-the-premises build, Australia’s government was dealing with an obstructionist and hostile Telstra, Australia’s dominant telco. Under the “three amigos” led by CEO Sol Trujillo (the other two were Phil Burgess and Bill Stewart, both from Trujillo’s time at US West), Telstra was trying to block the Australian Competition and Consumer Commission’s competitive regulatory interventions (wth High Court action), and delaying or white-anting government attempts to encourage high-speed broadband.
The government of the day conceived its NBN in part to unblock the regulatory deadlocks – but it needed to fund the network and didn’t want the cost to be directly attributed to the federal budget.
One of the documents reveals the range of funding options brought to cabinet. As well as the government’s eventual model of investing equity in NBN Co, various bond sales were considered. The bond options included letting retail investors in at an attractive rate; or long-term infrastructure bonds.

If Australian animals don’t poison you or eat you, they’ll BURN DOWN YOUR HOUSE
The government of the day also had hopes that Telstra would buy into the build, since the NBN’s customer access network would replace its own.
The document entitled “Strategy for negotiating with potential investors in NBN Co” states “there are likely to be many early approaches by a range of possible investors, including Telstra”.
However, the cabinet briefing also stated that nobody would buy in “until the details of the company and the regulatory framework (and, in all likelihood, the legislation) are settled”.
This didn’t bother the government of the day too much, it seems, since its intention was to privatise the network after build: “the Government does not need to rush into negotiations with investors making early offers”, the paper states.
The government had some hope that the existence of NBN Co would make Telstra more co-operative (and, perhaps, offer a chance for a change in strategy).
“The ideal outcome, over time, is the structural separation of Telstra by action of the Board”, the paper states, while noting that an intransigent Telstra might “choose to compete … using platforms such as the HFC network”.
With a fully structurally-separated Telstra, the document shows, the government had no trouble contemplating investment in NBN Co from Telstra Wholesale: before the network was completed, the government would remain its majority shareholder and therefore able to protect retail customers.
Nearly all of those discussions are now moot, since the network that now exists isn’t a particularly saleable asset.
The government was also acutely aware of the kinds of things Telstra would want if it were given a free hand in negotiations. The establishment of NBN Co and its wholesale-only status was non-negotiable from the start; Telstra might want to fold in assets like duct access which would be capped; the carrier would not be given a voice in matters like NBN access, price, rollout timing, and the government clearly expected it to lobby against fibre-to-the-premises.
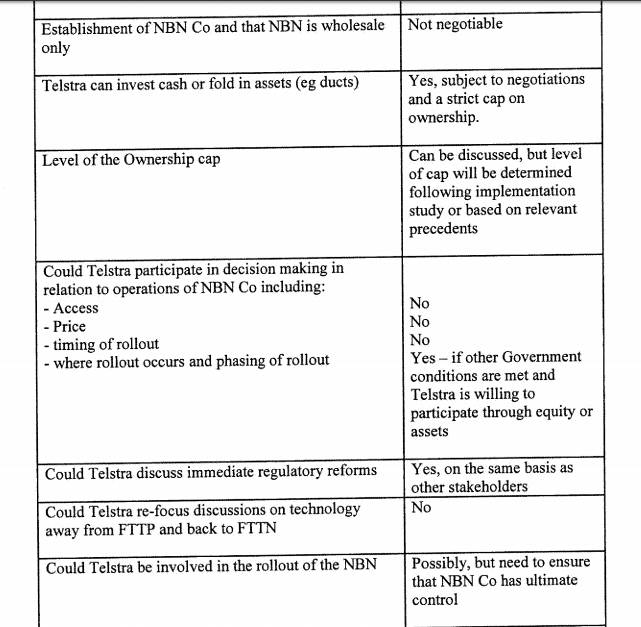
The Rudd government knew Telstra was likely to be troublesome. Image: the Australian Broadcasting Corporation
Telstra was expected to lobby the government over regulation, something the government wanted nixed, but it would (as has since happened) be allowed to take part in the rollout.
Vulture South will keep our eyes on the cabinet leaks to look for other snippets of interest to our readers. And for chances to point-and-laugh at the government. ®
Sponsored:
Minds Mastering Machines – Call for papers now open
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2018/01/31/australian_cabinet_leaked_a_cabinet/
