Tinder user? Lack of encryption means stalkers can watch you at it…
You may never have used Tinder, but you’ve probably heard of it.
We’re not quite sure how to describe it, but the company itself offers the following official About Tinder statement:
The people we meet change our lives. A friend, a date, a romance, or even a
chance encounter can change someone’s life forever. Tinder empowers users around the world to create new connections that otherwise might never have been possible. We build products that bring people together.
That’s about as clear as mud, so to keep it simple, let’s just describe Tinder as a dating-and-hookup app that helps you find people to party with in your immediate vicinity.
Once you’ve signed up and given Tinder access to your location and information about your lifestyle, it calls home to its servers and fetches a bunch of images of other Tinderers in your area. (You choose how far afield it should search, what age group, and so on.)
The images appear one after the other and you swipe left if you don’t like the look of them; right if you do.
The people you swipe to the right get a message that you fancy them, and the Tinder app takes care of the messaging from there.
A whole lot of dataflow
Dismiss it as a cheesy idea if you like, but Tinder claims to process 1,600,000,000 swipes a day and to set up 1,000,000 dates a week.
At more than 11,000 swipes per date, that means that a lot of data is flowing back and forth between you and Tinder while you search for the right person.
You’d therefore like to think that Tinder takes the usual basic precautions to keep all those images secure in transit – both when other people’s images are being sent to you, and yours to other people.
By secure, of course, we mean making sure not only that the images are transmitted privately but also that they arrive intact, thus providing both confidentiality and integrity.
Otherwise, a miscreant/crook/stalker/creep in your favourite coffee shop would easily be able to see what you were up to, as well as to modify the images in transit.
Even if all they wanted to do was to freak you out, you’d expect Tinder to make that as good as impossible by sending all its traffic via HTTPS, short for Secure HTTP.
Well, researchers at Checkmarx decided to check whether Tinder was doing the right thing, and they found that when you accessed Tinder in your web browser, it was.
But on your mobile device, they found that Tinder had cut security corners.
We put the Checkmarx claims to the test, and our results corroborated theirs.
As far as we can see, all Tinder traffic uses HTTPS when you use your browser, with most images downloaded in batches from port 443 (HTTPS) on images-ssl.gotinder.com.
The images-ssl domain name ultimately resolves into Amazon’s cloud, but the servers that deliver the images only work over TLS – you simply can’t connect to plain old http://images-ssl.gotinder.com because the server won’t talk plain old HTTP.
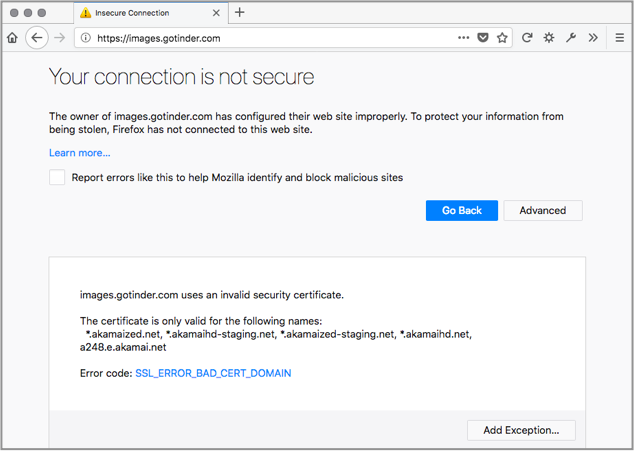
Switch to the mobile app, however, and the image downloads are done via URLs that start with http://images.gotinder.com, so they are downloaded insecurely – all the images you see can be sniffed or modified along the way.
Ironically, images.gotinder.com does handle HTTPS requests via port 443, but you’ll get a certificate error, because there’s no Tinder-issued certificate to go with the server:
The Checkmarx researchers went further still, and claim that even though each swipe is conveyed back to Tinder in an encrypted packet, they can nevertheless tell whether you swiped left or right because the packet lengths are different.
Differentiating left/right swipes shouldn’t be possible at any time, but it’s a much more serious data leakage problem when the images you’re swiping on have already been revealed to your nearby creep/stalker/crook/miscreant.
What to do?
We can’t figure out why Tinder would program its regular website and its mobile app differently, but we have become accustomed to mobile apps lagging behind their desktop counterparts when it comes to security.
So…
- For Tinder users: if you are worried about how much that creep in the corner of the coffee shop might learn about you by eavesdropping on your Wi-Fi connection, stop using the Tinder app and stick to the website instead.
- For Tinder programmers: you’ve got all the images on secure servers already, so stop cutting corners (we’re guessing you thought it would speed the mobile app up a bit to have the images unencrypted). Switch your mobile app to use HTTPS throughout.
- For software engineers everywhere: don’t let the product managers of your mobile apps take security shortcuts. If you outsource your mobile development, don’t let the design team convince you to let form run ahead of function.
Follow @NakedSecurity
Follow @duckblog
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/6fZLq-p0rjA/