Free ESG report : Seamless data management with Avere FXT
Microsoft’s promotion of visual passwords, based on tapping pictures and making gestures instead of conventional text passwords, might be a boon for usability. Yet security experts warn the technology is less secure than even a simple 4-digit PIN.
The increased power of brute force attacks, password hash database leaks and the difficulty of getting users to choose secure text passwords in the first place means that attempts to create alternative login techniques are well worth exploring.
Windows 8 and Windows RT come with a feature called Picture Passwords. Users can choose any picture, and then “annotate” it with three finger movements: tapping a point, drawing a stroke, or sweeping a circle. This pattern becomes a users’ means to open or unlock a device as an alternative to a text password or PIN unlock code.
The picture helps you to remember where you made the gestures, so you can repeat them reliably enough to pass the test and unlock your device.
Tap, tap, pinto, stroke. Hack?
Four security researchers from Arizona State University and Delaware State University tried to measure the safety of picture passwords in a research paper, titled On the Security of Picture Gesture Authentication (PDF). The paper was presented at last month’s USENIX Security Symposium (summary and video here).
Microsoft’s own paper on the design, implementation and likely strength of picture passwords estimates that there are just over 1.155 billion possible picture passwords if three gestures are used.
The sounds like a lot, but is “only about four times as many as there are six-character passwords using the characters A to Z,” says security watcher Paul Ducklin. “No-one is seriously suggesting six-character, letters-only passwords these days,” he notes in a post on Sophos’s Naked Security blog.
“Furthermore, the equivalent of a dictionary attack is possible, too, if you can identify the most likely Points of Interest (PoIs) in the password picture. So a brute force attack is certainly possible, where you ignore the picture entirely and just try every possible tap-click-circle combination,” he adds.
All is not lost, however. Like credit cards that automatically block after three failed PIN entry attempts, making five mistakes in inputting a picture password obliges users to switch to using an old-fashioned text password. This, combined with the need for physical access to the device, limits the potential for potential misuse.
Can you see what it is yet?
The weakness, according to the researchers behind the USENIX paper, is that the point of interest in a picture users might tap on and the gesture they might make can be guessed. Microsoft’s own ad for picture passwords features a picture of someone’s two young daughters, heads close together and looking at some distant object. The password involved circling their heads and then drawing a line in the direction they were looking.
The chosen pattern is easily guessed. Using a test set of just over 10,000 passwords and 800 subjects, the Arizona State University and Delaware State University team reckon that automated point of recognition and other techniques can be used to guess visual gesture-based passwords correctly in 19 out of 1000 cases, given five attempts. The first guess alone would work in around nine in 1000 cases. Manual point of interest recognition offers even better results with a 26 in 1000 chance of hitting on the right gesture within five attempts.
So the security of picture passwords is a lot less than the three-in-10,000 chance of correctly guessing a randomly chosen four-digit SIM or credit card PIN before subsequent re-tries are blocked. In practice, however device unlock numbers are often not chosen randomly; something that limits their security.
Picture this
Picture gesture authentication has many of the same limitations of text passwords, as a blog post by Kaspersky Labs’ Threatpost news service notes. The computer scientists behind the USENIX research urge Microsoft and other suppliers to be more upfront to users about this point, as well as developing tools to provide an indication of the strength of visual passwords, similar to text password strength meters.
Those not deterred by these figures and still attracted by convenience of gesture-based visual passwords would be well advised to select hard-to-guess picture passwords.
“If you use Picture Passwords, don’t make it easy for the crooks: choose pictures with lots of PoIs, and don’t just ‘do the obvious’ when you choose the gestures you’re going to use,” Ducklin advises.
Microsoft itself offers tips on picking a secure picture password.
Per Thorsheim, an independent security consultant, who runs a set of conferences about password security, has a good overview of the multiple password options bundles with Windows 8 here.
Mapping function
Security researchers have shown how to extract passwords, hashes and password hints from Windows 8. Extracting PIN and picture password data might also be possible, and this wouldn’t need any attempt at guessing picture passwords. Both Ducklin and Thorsheim expressed interest in seeing more research into this area of offline attacks.
“How Picture Password data is stored, and how password attempts are tested against the database, is proprietary,” Ducklin writes. “With an effective key size of just 30 bits, it is vital to set a very high cost for testing each potential password against an offline copy of the password database. That requires a computationally expensive Key Derivation Function (KDF).”
Ducklin called on Microsoft should go public on how Picture Passwords work, from how they’re stored to how the KDF is calculated.
“You’d let outside experts assess the risk of offline attacks, which would be technically valuable. And you’d get great positive publicity for openness, considering the current brouhaha facing proprietary software vendors over the cryptographic influence of the world’s intelligence services,” he writes. ®
Free ESG report : Seamless data management with Avere FXT
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2013/09/13/picture_passwords/
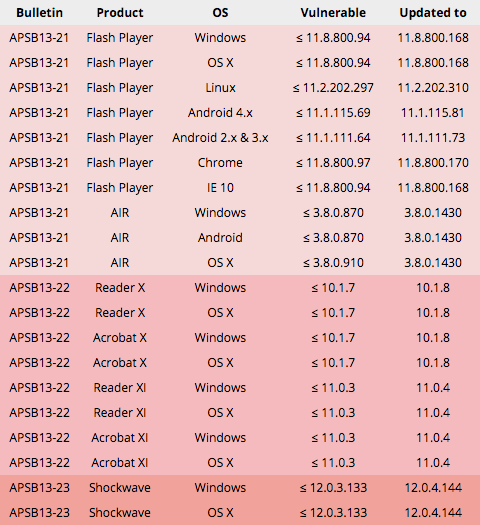
 Mega-popular blogging and content management system WordPress has just put out version 3.6.1.
Mega-popular blogging and content management system WordPress has just put out version 3.6.1.
 57% of college students view their Facebook postings through rose-tinted glasses, blithely seeing nothing inappropriate.
57% of college students view their Facebook postings through rose-tinted glasses, blithely seeing nothing inappropriate. If college students need further help with keeping safe on Facebook, as in, keeping safe their chances of ever getting hired, it would behoove them to take a peek at one site that collates
If college students need further help with keeping safe on Facebook, as in, keeping safe their chances of ever getting hired, it would behoove them to take a peek at one site that collates  I’m calling it a
I’m calling it a 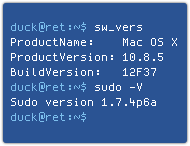 Confusingly, if you run sudo -V to check the version number, you might get the impression it hasn’t been updated, since 1.7.4p6a has the same core version string as the version shipped with 10.8.4 (1.7.4p6).
Confusingly, if you run sudo -V to check the version number, you might get the impression it hasn’t been updated, since 1.7.4p6a has the same core version string as the version shipped with 10.8.4 (1.7.4p6). That’s the bug we
That’s the bug we  Neither Lion nor Mountain Lion need or receive this fix, as they are on Safari 6.
Neither Lion nor Mountain Lion need or receive this fix, as they are on Safari 6. London Metropolitan Police are
London Metropolitan Police are  Of course, even with access to a workstation, there’s no telling how much further the crooks would have got.
Of course, even with access to a workstation, there’s no telling how much further the crooks would have got.  I’m calling it a
I’m calling it a 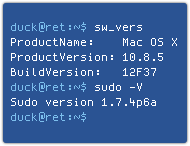 Confusingly, if you run sudo -V to check the version number, you’ll get the impression it hasn’t been updated, since 1.7.4p6a is the same as the version shipped with 10.8.4, and is officially listed by the sudo project as vulnerable.
Confusingly, if you run sudo -V to check the version number, you’ll get the impression it hasn’t been updated, since 1.7.4p6a is the same as the version shipped with 10.8.4, and is officially listed by the sudo project as vulnerable. That’s the bug we
That’s the bug we