Hash of the Titan: How Google bakes security all the way into silicon
Google has unveiled more details about how security built into its custom silicon chips underpins the integrity of its servers and cloud-based services.
A blog post details how Google’s custom Titan chip provides a hardware-verified boot and end-to-end authenticated root of trust for the internet giant’s computing workhorses.
“We harden our architecture at multiple layers, with components that include Google-designed hardware, a Google-controlled firmware stack, Google-curated OS images, a Google-hardened hypervisor, as well as data center physical security and services,” the team of senior Google techies explain.
Titan is a secure, low-power micro-controller specially designed with Google hardware security requirements which was first announced at Google Cloud Next ’17 back in March.
The chip is a continuation of a longer running security philosophy involving building security in custom silicon for Google servers previously covered by The Register back in January.
Titan is designed to ensure a machine boots from a known good state using verifiable code, providing a secure foundation for subsequent operations and all but eliminating the possibility of firmware-based rootkits or other similar nasties.
“Our [data center] machines boot a known firmware/software stack, cryptographically verify this stack and then gain (or fail to gain) access to resources on our network based on the status of that verification. Titan integrates with this process and offers additional layers of protection,” the Google team writes.
Secure boot typically relies on a combination of an authenticated boot firmware and boot loader along with digitally signed boot files. In addition, a secure element can provide private key storage and management. Titan then offers two extra security controls – remediation and first-instruction integrity.
Remediation offers a way to re-establish trust in cases where bugs in Titan firmware are found and patched. First-instruction integrity allows Google to identify the earliest code that runs on each machine’s startup cycle.
Titan bundles several components: a secure application processor, a cryptographic co-processor, a hardware random number generator, a key hierarchy, embedded static RAM (SRAM), embedded flash and a read-only memory block.
In effect, Google is pushing verification of secure boot for its hardware all the way down the stack and onto bare-metal silicon. Google is taking a belt, braces and elasticated waistband approach to delivering secure boot – and it’s relying on in-house expertise rather than third parties to deliver this technology.
“[It’s] clearly worried about supply chain,” University of York techie Arthur Clune suggests.
As Clune notes, the recent Black Hat conference in Las Vegas research on firmware vulnerabilities (PDF) might be used to plant software backdoors. Google acknowledges such outside interference as a risk it is trying to exclude.
Google designed Titan’s hardware logic in-house to reduce the chances of hardware backdoors. The Titan ecosystem ensures that production infrastructure boots securely using authorized and verifiable code.
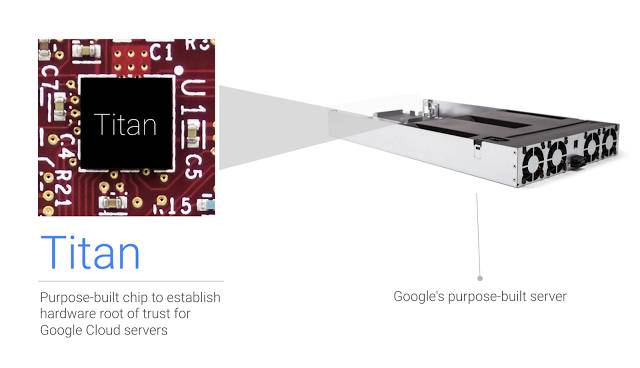
The custom Titan chip and how it fits inside Google’s purpose-built server [source: Google]
In addition to enabling secure boot, Google has developed an end-to-end cryptographic identity system based on Titan that offers a root of trust for varied cryptographic operations in its data centers. The system’s strong identity gives Google a non-repudiable audit trail of any changes done to the system. Tamper-evident logging capabilities are there to help identify actions performed even by an insider with root access.
Titan provides a root of trust by enabling verification of the system firmware and software components as well as establishing a strong, hardware-rooted system identity, Google concludes. ®
Sponsored:
The Joy and Pain of Buying IT – Have Your Say
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2017/08/25/google_titan_security_silicon/



